Kamagra gibt es auch als Kautabletten, die sich schneller auflösen als normale Pillen. Manche Patienten empfinden das als angenehmer. Wer sich informieren will, findet Hinweise unter kamagra kautabletten.
07-rewerse-ss-policies-07-04-30-camera_ready.dvi
Rule-Based Policy Representation andReasoning for the Semantic Web
Piero A. Bonatti and Daniel Olmedilla
a di Napoli Federico II, Napoli, Italy
L3S Research Center and University of
[email protected]
Summary. The Semantic Web aims at enabling sophisticated and autonomic ma-chine to machine interactions without human intervention, by providing machinesnot only with data but also with its meaning (semantics). In this setting, traditionalsecurity mechanisms are not suitable anymore. For example, identity-based accesscontrol assumes that parties are known in advance. Then, a machine first determinesthe identity of the requester in order to either grant or deny access, depending on itsassociated information (e.g., by looking up its set of permissions). In the SemanticWeb, any two strangers can interact with each other automatically and thereforethis assumption does not hold. Hence, a semantically enriched process is requiredin order to regulate an automatic access to sensitive information. Policy-based ac-cess control provides sophisticated means in order to support protecting sensitiveresources and information disclosure.
However, the term policy is often overloaded. A general definition might be "a
statement that defines the behaviour of a system". However, such a general defi-nition encompasses different notions, including security policies, trust managementpolicies, business rules and quality of service specifications, just to name a few. Re-searchers have mainly focussed on one or more of such notions separately but noton a comprehensive view. Policies are pervasive in web applications and play crucialroles in enhancing security, privacy, and service usability as well. Interoperability andself-describing semantics become key requirements and here is where Semantic Webcomes into play. There has been extensive research on policies, also in the SemanticWeb community, but there still exist some issues that prevent policy frameworksfrom being widely adopted by users and real world applications.
This document aims at providing an overall view of the state of the art (require-
ments for a policy framework, some existing policy frameworks/languages, policynegotiation, context awareness, etc.) as well as open research issues in the area (pol-icy understanding in a broad sense, integration of trust management, increase insystem cooperation, user awareness, etc.) required to develop a successful SemanticPolicy Framework.
Piero A. Bonatti and Daniel Olmedilla
Information provided in the current Web is mainly human oriented. For example,HTML pages are human understandable but a computer is not able to understandthe content and extract the right concepts represented there, that is, the meaning ofthe data. The Semantic Web [1] is a distributed environment in which informationis self-describable by means of well-defined semantics, that is, machine understand-able, thus providing interoperability (e.g., in e-commerce) and automation (e.g., insearch). In such an environment, entities which have not had any previous inter-action may now be able to automatically interact with each other. For example,imagine an agent planning a trip for a user. It needs to search for and book a planeand a hotel taking into account the user's schedule. When the user's agent contacts ahotel's website, the latter needs to inform the former that it requires a credit card inorder to confirm a reservation. However, the user may probably want to restrict theconditions under which her agent automatically discloses her personal infomation.
Due to such exchange of conditions and personal information, as well as its automa-tion, security and privacy become yet more relevant and traditional approaches arenot suitable anymore. On the one hand, unilateral access control is now replaced bybilateral protection (e.g., not only the website states the conditions to be satisfiedin order to reserve a room but also the user agent may communicate conditions un-der which a credit card can be disclosed). On the other hand, identity-based accesscontrol cannot be applied anymore since users are not known in advance. Instead,entities' properties (e.g., user's credit card or whether a user is a student) play acentral role. Both these properties and conditions stating the requirements to befulfilled by the other party, must be described in a machine-understandable lan-guage with well-defined semantics allowing other entities to process them. Systemssemantically annotated with policies enhance their authorisation process allowing,among others, to regulate information disclosure (privacy policies), to control accessto resources (security policies), and to estimate trust based on parties' properties(trust management policies) [2].
Distributed access control has addressed some of these issues though not com-
pletely solved them yet. Examples like KeyNote [3] or PolicyMaker [4] provide aseparation between enforcement and decision mechanisms by means of policies. How-ever, policies are bound to public keys (identities) and are not expressive enoughto deal with Semantic Web scenarios. RBAC (Role-Based Access Control) also doesnot meet Semantic Web requirements since it is difficult to assign roles to userswhich are not known in advance. Regarding to user's privacy protection, Platformfor Privacy Preferences (P3P) provides a standard vocabulary to describe Web serverpolicies. However, it is not expressive enough (it is a schema, not a language, andonly describes purpose for the gathered data) and it does not allow for enforcementmechanisms. On the other hand, there is a wide offer of policy languages that havebeen developed to date [5, 6, 7, 8], addressing the general requirements for a Seman-tic Web policy language: expressiveness, simplicity, enforceability, scalability, andanalyzability [9]. These policies can be exchanged between entities on the SemanticWeb and therefore they are described using languages with well-founded semantics.
The policy languages listed above differ in expressivity, kind of reasoning re-
quired, features and implementations provided, etc. For the sake of simplicity, theyare divided according to their protocol for policy exchange between parties, depend-ing on the sensitivity of policies. On the one hand, assuming that all policies are
Rule-Based Policy Representation and Reasoning for the Semantic Web
public and accessible (typical situation in many multi-agent systems), the processof evaluating whether two policies from two different entities are compatible or notconsists in gathering the relevant policies (and possibly relevant credentials) fromthe involved entities and checking whether they match (e.g., [10]). On the otherhand, if policies may be private (typical situation for business rules [11]), it impliesthat not all policies are known in advance but they may be disclosed at a laterstage. Therefore, a negotiation protocol in which security and trust is iterativelyestablished is required [12].
However, specifying policies is as difficult as writing imperative code, getting a
policy right is as hard as getting a piece of software correct, and maintaining a largenumber of them is even harder. Fortunately, ontologies and policy reasoning mayhelp users and administrators on specification, conflict detection and resolution ofsuch policies [5, 13].
As it can be seen, there has been extensive research in the area, including the
Semantic Web community, but several aspects still exist that prevent policy frame-works from widespread adoption and real world application. This manuscript incor-porates and merges the ideas of previosly published papers [14, 2, 15] and aims atproviding an overall view of the state of the art (requirements for a policy framework,some existing policy frameworks/languages, policy negotiation, context awareness,etc.) as well as open research issues in the area (policy understanding in a broadsense, integration of trust management, increase in system cooperation, user aware-ness, etc.) required to develop a successful Semantic Policy Framework. Section 2describes how policies are exchanged and how they interact among parties on theSemantic Web, with a brief description of the main Semantic Web policy languagesand how ontologies may be used in policy specification, conflict detection and valida-tion. Some examples of application scenarios are presented in Section 3, where policybased security and privacy are used. Section 4 discusses important requirements andopen research issues in this context, focusing on policies in general and their inte-gration into trust management frameworks, as well as on approaches to increasesystem cooperation, usability and user-awareness of policy issues. This manuscriptfinally concludes with a last section (Section 5) in which the most important isssuespresented are summarized.
2 Policy Based Interaction and Evaluation
Policies allow for security and privacy descriptions in a machine understandableway. More specifically, service or information providers may use security policies tocontrol access to resources by describing the conditions a requester must fulfil (e.g.,a requester to resource A must belong to institution B and prove it by means of acredential). At the same time, service or information consumers may regulate theinformation they are willing to disclose by protecting it with privacy policies (e.g., anentity is willing to disclose its employee card credential only to the web server of itsemployer). Given two sets of policies, an engine may check whether they are compat-ible, that is, whether they match. The complexity of this process varies dependingon the sensitivity of policies (and the expressivity of the policies). If all policies arepublic at both sides (typical situation in many multi-agent systems), provider andrequester, the requester may initially already provide the relevant policies together
Piero A. Bonatti and Daniel Olmedilla
with the request and the evaluation process can be performed in a one-step evalua-tion by the provider policy engine (or an external trusted matchmaker) and returna final decision. Otherwise, if policies may be private, as it is, for example, typi-cally the case for sensitive business rules, this process may consist of several stepsnegotiation in which new policies and credentials are disclosed at each step, there-fore advancing after each iteration towards a common agreement. In this section wegive an overview of both types of languages. The main features of these languagesare shown in Table 1. Additionally, we use the running policy "only employees ofinstitution XYZ may retrieve a file" to illustrate an example of each language.
2.1 One-Step Policy Evaluation
Assuming that policies are publicly disclosable, there is no reason why a requestershould not disclose its relevant applicable policies together with its request. This way,the provider's policy engine (or a trusted external matchmaker in case the providerdoes not have one) has all the information needed to make an authorisation decision.
The KAOS and REI frameworks, specially designed using Semantic Web featuresand constructs, fall within this category of policy languages, those which do notallow policies themselves to be protected.
Table 1. Comparison of KAOS, REI, PeerTrust and Protune3
Authorization Reasoning
DL + vari- Dinamyc detec- Used
tion & resolu- conflict reso-tion
KAOS Policy and Domain Services
KAOS Services [5, 16] provide a framework for specification, management, conflictresolution and enforcement of policies allowing for distributed policy interactionand support for dynamic policy changes. It uses OWL [17] ontologies (defining e.g.
actors, groups and actions) to describe the policies and the application context,and provides administration tools (KAOS Administration Tool - KPAT) to helpadministrators to write down their policies and hide the complexity of using OWLdirectly. A policy in KAOS may be a positive (respectively negative) authorisation,
Rule-Based Policy Representation and Reasoning for the Semantic Web
i.e., constraints that permit (respectively forbid) the execution of an action, or apositive (respectively negative) obligation, i.e., constraints that require an action tobe executed (respectively waive the actor from having to execute it). A policy isthen represented as an instance of the appropriate policy type, associating values toits properties, and giving restrictions on such properties (Figure 1 sketches part ofa KAOS policy).
KAOS benefits from the OWL representation and description logic based sub-
sumption mechanisms [18]. Thus, it allows to, for example, obtain all known sub-classes or instances of a class within a given range (used during policy specificationto help users choosing only valid classes or instances) or detect policy conflicts (bychecking disjointness of subclasses of the action class controlled by policies). KAOSis able to detect three types of conflicts, based on the types of policies that areallowed in the framework: positive vs. negative authorisation (a policy allows ac-cess and but another denies it), positive vs. negative obligation (a policy obliges toexecute an action while another dispensates from such obligation) and positive obli-gation vs. negative authorisation (a policy obliges to execute an action but anotherdenies authorisation for such execution). KAOS resolves such conflics (also calledharmonisation) based on assigning preferences to policies and resolving in favour ofthe policies with higher priority (Section 2.3 will later extend on this).
Finally, KAOS assumes a default authorisation mechanism in case no policy
applies to a request. It can be either "permit all actions not explicitly forbidden" or"forbid all actions not explicitly authorised".
Fig. 1. Example of KAOS policies
3 DL refers to Description Logic while LP stands for Logic Programming
Piero A. Bonatti and Daniel Olmedilla
REI 2.0 [19, 10] expresses policies according to what entities can or cannot do andwhat they should or should not do. They define an independent ontology whichincludes the concepts for permissions, obligations, actions, etc. Additionally, as inKAOS, they allow the import of domain dependent ontologies (including domaindependent classes and properties). REI 2.0 is represented in OWL-Lite and includeslogic-like variables in order to specify a range of relations.
REI policies (see Figure 2 for an example) are described in terms of deontic
concepts: permissions, prohibitions, obligations and dispensations, equivalently tothe positive/negative authorisations and positive/negative obligations of KAOS. Inaddition, REI provides a specification of speech acts for the dynamic exchange ofrights and obligations between entities: delegation (of a right), revocation (of apreviously delegated right), request (for action execution or delegation) and cancel(of a previous request).
As in the KAOS framework, REI policies may conflict with each other (right
vs. prohibition or obligation vs. dispensation). REI provides mechanisms for conflictdetection and constructs to resolve them, namely, overriding policies (similar tothe prioritisation in KAOS) and definition at the meta-level of the global modality(positive or negative) that holds (see Section 2.3 for more details).
Fig. 2. Example of REI policies
2.2 Policy-Driven Negotiations
In the approaches presented previously, policies are assumed to be publicly disclos-able. This is true for many scenarios but there exist other scenarios where it may nothold. For example, imagine a hospital revealing to everyone that in order to receiveAlice's medical report, the requester needs an authorisation from Alice's psychia-trist. Another example, imagine Tom wants to share his holiday pictures on-line
Rule-Based Policy Representation and Reasoning for the Semantic Web
only with his friends. If he states publicly that policy and Jessica is denied access,she may get angry because of Tom not considering her as a friend. Moreover, policyprotection becomes even more important when policies protects sensitive businessrules.
These scenarios require the possibility to protect policies (policies protecting
policies) and the process of finding a match between requester and provider be-comes more complex, since not all relevant policies may be available at the time.
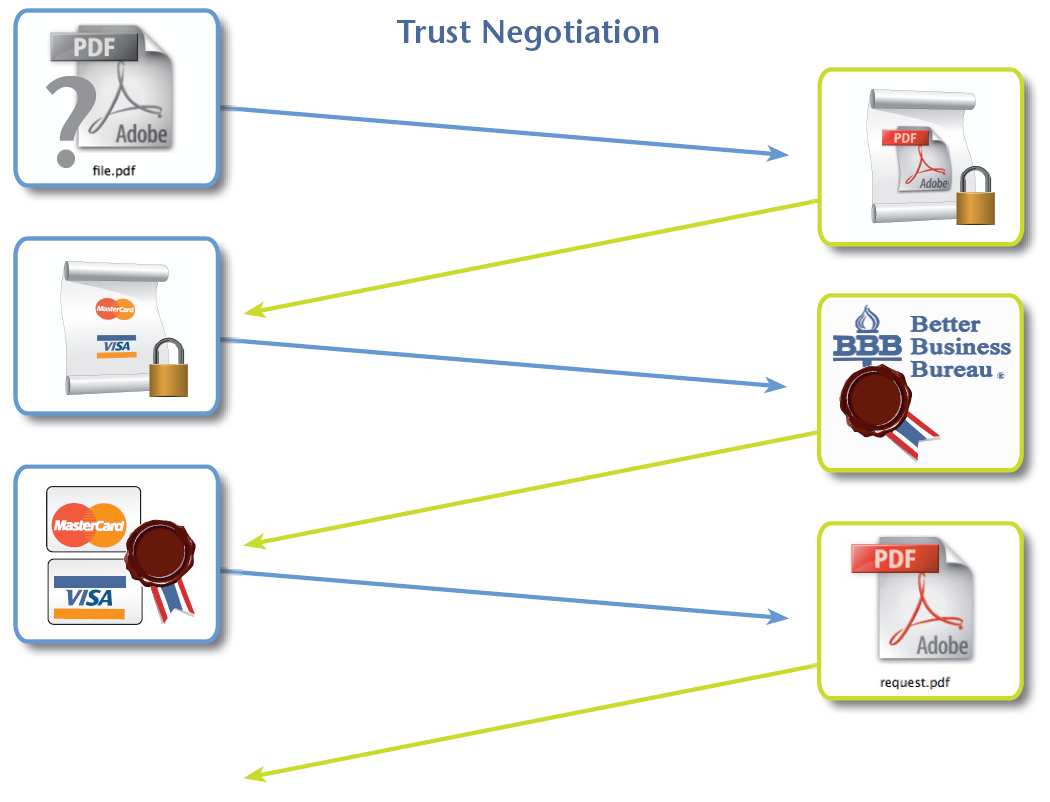
Therefore, this process may consist of a several steps negotiation, by disclosing newpolicies and credentials at each step, and therefore advancing after each iterationtowards a common agreement [12]. For example, suppose Alice requests access to aresource at e-shop. Alice is told that she must provide her credit card to be grantedaccess. However, Alice does not want to disclose her credit card just to anyone andshe communicates to e-shop that before it gets her credit card, it should provideits Better Business Bureau certification. Once e-shop discloses it, Alice's policy isfulfilled and she provides the credit card, thus fulfilling e-shop's policy and receivingaccess to the requested resource (see Figure 3).
Fig. 3. Policy-driven negotiation between Alice and e-shop
Below, the two most recent languages for policy-driven negotiation are presented.
They are also specially designed for the Semantic Web. However, we refer the in-terested reader to other languages for policy based negotiations [20, 21, 22], whichmay be applied to the Semantic Web.
PeerTrust [7] builds upon previous work on policy-based access control and releasefor the Web and implements automated trust negotiation for such a dynamic envi-ronment.
PeerTrust's language is based on first order Horn rules (definite Horn clauses),
i.e., rules of the form "lit0 ← lit1, . . , litn" where each liti is a positive literal
Piero A. Bonatti and Daniel Olmedilla
Pj (t1, . . , tn), Pj is a predicate symbol, and the ti are the arguments of this predi-cate. Each ti is a term, i.e., a function symbol and its arguments, which are them-selves terms. The head of a rule is lit0, and its body is the set of liti. The body ofa rule can be empty.
Definite Horn clauses can be easily extended to include negation as failure, re-
stricted versions of classical negation, and additional constraint handling capabilitiessuch as those used in constraint logic programming. Although all of these featurescan be useful in trust negotiation, here are only described other more unusual re-quired language extensions. Additionally, PeerTrust allows the import of RDF basedmeta-data therefore allowing the use of ontologies within policy descriptions.
retrieveFile(fileXYZ ) $ Requester ← employed(Requester) @ institutionXYZ .
Fig. 4. Example of PeerTrust policies
References to Other Peers PeerTrust's ability to reason about statements madeby other peers is central to trust negotiation. To express delegation of evaluation toanother peer, each literal liti is extended with an additional Authority argument,that is
where Authority specifies the peer who is responsible for evaluating liti or has the
authority to evaluate liti. The Authority argument can be a nested term containinga sequence of authorities, which are then evaluated starting at the outermost layer.
A specific peer may need a way of referring to the peer who asked a particular
query. This is accomplished by including a Requester argument in literals, so thatnow literals are of the form
liti @ Issuer $ Requester
The Requester argument can also be nested, in which case it expresses a chain ofrequesters, with the most recent requester in the outermost layer of the nested term.
Using the Issuer and Requester arguments, it is possible to delegate evalua-
tion of literals to other parties and also express interactions and the correspondingnegotiation process between parties (see Figure 4 for an example).
Signed Rules Each peer defines a policy for each of its resources, in the form of aset of definite Horn clause rules. These and any other rules that the peer defineson its own are its local rules. A peer may also have copies of rules defined by otherpeers, and it may use these rules to generate proofs, which can be sent to otherentities in order to give evidence of the result of a negotiation.
Rule-Based Policy Representation and Reasoning for the Semantic Web
A signed rule has an additional argument that says who signed the rule. The
cryptographic signature itself is not included in the policy, because signatures arevery large and are not needed by this part of the negotiation software. The signatureis used to verify that the issuer really did issue the rule. It is assumed that whena peer receives a signed rule from another peer, the signature is verified before therule is passed to the DLP evaluation engine. Similarly, when one peer sends a signedrule to another peer, the actual signed rule must be sent, and not just the logicprogrammatic representation of the signed rule. More complex signed rules oftenrepresent delegations of authority.
Loop detection mechanisms In declarative policy specification, loops may easily
occur and should not be considered as errors. For example, declarative policies maystate at the same time that "anyone with write permissions can read a file" and"anyone with read permissions can write a file". If not handled accordingly, suchloops may end up in non-terminating evaluation [23]. In practice, policies, includingfor instance business rules, are complex and large in number (and typically not un-der control of a single person) which increases the risk of loops and non-terminationduring dynamic policy evaluation. A distributed tabling algorithm can handle safelymutual recursive dependencies (loops) in distributed environments. Due to the se-curity context, other aspects like private and public policies and proof generationmust be taken into account [23].
The PRovisional TrUst NEgotiation framework Protune [8] aims at combining dis-tributed trust management policies with provisional-style business rules and access-control related actions. Protune's rule language extends two previous languages:PAPL [20], which until 2002 was one of the most complete policy languages fortrust negotiation, and PeerTrust [7], which supports distributed credentials and amore flexible policy protection mechanism. In addition, the framework features apowerful declarative meta-language for driving some critical negotiation decisions,and integrity constraints for monitoring negotiations and credential disclosure.
access(‘fileXYZ') ← credential(employee, C), C.type:employee_id, C.affiliation :‘XYZ'.
access(_).type:decision.
access(_).sensitivity :public.
Fig. 5. Example of Protune policies
Protune provides a framework with:
A trust management language supporting general provisional-style4 actions (pos-sibly user-defined).
4 Authorizations involving actions and side effects are sometimes called provisional.
Piero A. Bonatti and Daniel Olmedilla
An extendible declarative meta-language for driving decisions about request for-mulation, information disclosure, and distributed credential collection.
A parameterised negotiation procedure, that gives a semantics to the meta-language and provably satisfies some desirable properties for all possible meta-policies.
Integrity constraints for negotiation monitoring and disclosure control.
General, ontology-based techniques for importing and exporting meta-policiesand for smoothly integrating language extensions.
Advanced policy explanations in order to answer why, why-not, how-to, andwhat-if queries [24]
The Protune rule language is based on normal logic program rules "A ←
L1, . . , Ln" where A is a standard logical atom (called the head of the rule) andL1, . . , Ln (the body of the rule) are literals, that is, Li equals either Bi or ¬Bi, forsome logical atom Bi.
A policy is a set of rules (see Figure 5 for an example), such that negation
is applied neither to provisional predicates (defined below), nor to any predicateoccurring in a rule head. This restriction ensures that policies are monotonic oncredentials and actions, that is, as more credentials are released and more actionsexecuted, the set of permissions does not decrease.
The vocabulary of predicates occurring in the rules is partitioned into the follow-
ing categories: Decision Predicates (currently supporting "allow()" which is queriedby the negotiation for access control decisions and "sign()" which is used to issuestatements signed by the principal owning the policy, Abbreviation Predicates (asdescribed in [20]), Constraint Predicates (which comprise the usual equality anddisequality predicates) and State Predicates (which perform decisions according tothe state). State Predicates are further subdivided in State Query Predicates (whichread the state without modifying it) and Provisional Predicates (which may bemade true by means of associated actions that may modify the current state likee.g. credential(), declaration(), logged(X, logf ile name)).
Furthermore, meta-policies consist of rules similar to object-level rules. They
allow to inspect terms, check groundness, call an object-level goal G against thecurrent state (using a predicate holds(G)), etc. In addition, a set of reserved at-tributes associated to predicates, literals and rules (e.g., whether a policy is publicor sensitive) is used to drive the negotiator's decisions. For example, if p is a pred-icate, then p.sensitivity : private means that the extension of the predicate isprivate and should not be disclosed. An assertion p.type : provisional declares pto be a provisional predicate; then p can be attached to the corresponding actionα by asserting p.action :α. If the action is to be executed locally, then we assertp.actor : self, otherwise assert p.actor : peer.
2.3 Policy specification, conflict detection and resolution
Previous sections described how the Semantic Web may benefit from the protectionof resources with policies specifying security and privacy constraints. However, spec-ifying policies may be as difficult as writing imperative code, getting a policy rightis as hard as getting a piece of software correct, and maintaining a large number ofthem is only harder. Fortunately, the Semantic Web can help administrators withpolicy specification, and detection and resolution of conflicts.
Rule-Based Policy Representation and Reasoning for the Semantic Web
Policy specification Tools like the KAOS Policy Administration Tool (K-PAT) [5]and the PeerTrust Policy Editor provide an easy to use application to help pol-icy writers. This is important because the policies will be enforced automaticallyand therefore errors in their specification or implementation will allow outsidersto gain inappropriate access to resources, possibly inflicting huge and costly dam-ages. In general, the use of ontologies on policy specification reduces the burdenon administrators, helps them with their maintenance and decreases the numberof errors. For example, ontology-based structuring and abstraction help maintaincomplex software, and so do they with complex sets of policies. In the context ofthe Semantic Web, ontologies provide a formal specification of concepts and theirinterrelationships, and play an essential role in complex web service environments,semantics-based search engines and digital libraries. Nejdl et al. [13] suggest us-ing two strategies to compose and override policies, building upon the notions ofmandatory and default policies, and formalising the constraints corresponding tothese kinds of policies using F-Logic. A prototype implementation as a Prot´eg´eplug-in shows that the proposed policy specification mechanism is implementableand effective.
Conflict detection and resolution. Semantic Web policy languages also allow foradvanced algorithms for conflict detection and its resolution. For example, in Sec-tion 2.1 it was briefly described how conflicts may arise between policies, either atspecification time or runtime. A typical example of a conflict is when several policiesapply to a request and one allows access while another denies it (positive vs. negativeauthorisation). Description Logic based languages may use subsumption reasoningto detect conflicts by checking if two policies are instances of conflicting types andwhether the action classes, that the policies control, are not disjoint. Both KAOSand REI handle such conflicts (like right vs. prohibition or obligation vs. dispensa-tion) within their frameworks and both provide constructs for specifying prioritiesbetween policies, hence the most important ones override the less important ones.
In addition, REI provides a construct for specifying a general modality priority:positive (rights override prohibitions and obligations override dispensations) or neg-ative (prohibitions override rights and dispensations override obligations). KAOSalso provides a conflict resolution technique called "policy harmonisation'. If a con-flict is detected the policy with lower priority is modified by refining it with theminimum degree necessary to remove the conflict. This process may generate zero,one or several policies as a refinement of the previous one (see [5] for more informa-tion). This process is performed statically at policy specification time ensuring thatno conflicts arise at runtime.
3 Applying Policies on the Semantic Web
The benefits of using semantic policy languages in distributed environments withautomated machine-machine interaction have been described extensible in previoussections. This section aims at providing some examples of its use in the context ofthe Web, (Semantic) Web Services and the (Semantic) Grid. In all cases, differentsolutions have been described addressing different scenarios from the point of viewof one-step authorization or policy-driven negotiations.
Piero A. Bonatti and Daniel Olmedilla
3.1 Policies on the Web
The current Web infrastructure does not allow the enforcement of user policies whileaccessing web resources. Web server authentication is typically based on authenti-cation mechanisms in which users must authenticate themselves (either by means ofcertificates or typing a user name and password). Semantic Web policies overcomesuch limitations of the Web.
Kagal et al. [6] describe how the REI language can be applied in order to control
access to web resources. Web pages are marked up with policies specifying whichcredentials are required to access such pages. A policy engine (bound to the webserver) decides whether the request matches the credentials requested. In case it doesnot, the web server could show which credentials are missing. Furthermore, Kolariet al. [25] presents an extension to the Platform for Privacy Preferences (P3P) usingthe REI language. The authors propose enhancements using REI policies to increasethe expressiveness and to allow for existing privacy enforcement mechanisms.
PeerTrust can be used to provide advanced policy-driven negotiations on the
Web in order to control access to resources [7, 26]. A user receives a signed (bya trusted authority) applet after requesting access to a resource. Such an appletincludes reasoning capabilities and is loaded in the Web browser. The applet au-tomatically imports the policies specified by the user and starts a negotiation. Ifthe negotiation succeeds, the applet simply retrieve the resource requested or, ifnecessary, redirects the user to the appropriate repository.
3.2 Semantic Web Services
Semantic Web Services aim at the automation of discovery, selection and compo-sition of Web Services. Denker et al. [27] and Kagal et al. [10] suggest extendingOWL-S with security policies, written in REI, like e.g. whether a service requires oris capable of providing secure communication channels. An agent may then submit arequest to the registry together with its privacy policies. The matchmaker at the reg-istry will filter out non-compatible service descriptions and select only those whosesecurity requirements of the service match the privacy policies of the requester.
Differently, Olmedilla et al. [28] propose the use of the PeerTrust language to
decide if trust can be established between a requester and a service provider dur-ing runtime selection of web services. Modelling elements are added to the WebService Modeling Ontology (WSMO) in order to include security information inthe description of Semantic Web Services. In addition, the authors discuss differentregistry architectures and their implications for the matchmaking process.
3.3 Semantic Grid
Grid environments provide the middleware needed for access distributed computingand data resources. Distinctly administrated domains form virtual organisations andshare resources for data retrieval, job execution, monitoring, and data storage. Suchan environment provides users with seamless access to all resources they are autho-rised to access. In current Grid infrastructures, in order to be granted access at eachdomain, user's jobs have to secure and provide appropriate digital credentials forauthentication and authorisation. However, while authentication along with single
Rule-Based Policy Representation and Reasoning for the Semantic Web
sign-on can be provided based on client delegation of X.509 proxy certificates to thejob being submitted, the authorisation mechanisms are still mainly identity-based.
Due to the large number of potential users and different certification authorities,this leads to scalability problems calling for a complementary solution to the accesscontrol mechanisms specified in the current Grid Security Infrastructure (GSI) [29].
Uszok et al. [30] presents an integration of the KAOS framework into Globus
Tookit 3. Its authors suggest offering a KAOS grid service and providing an interfaceso grid clients and services may register and check whether a specific action isauthorised or not. The KAOS grid service uses the KAOS policy services describedin Section 2.1 and relies on the Globus local enforcement mechanisms.
Alternatively, Constandache et al. [31] describe an integration of policy driven
negotiations for the GSI, using semantic policies and enhancing it providing auto-matic credential fetching and disclosure. Policy-based dynamic negotiations allowmore flexible authorisation in complex Grid environments, and relieve both usersand administrators from up front negotiations and registrations. Constandache etal. [31] introduces an extension to the GSI and Globus Toolkit 4.0 in which policy-based negotiation mechanisms offer the basis for overcoming these limitations. Thisextension includes property-based authorisation mechanisms, automatic gatheringof required certificates, bidirectional and iterative trust negotiation and policy basedauthorisation, ingredients that provide advanced self-explanatory access control togrid resources.
4 Requirements and Open Research Issues for aSemantic Web Policy Framework
Policies are pervasive in web applications. They play crucial roles in enhancingsecurity, privacy and usability of distributed services, and indeed may determinethe success (or failure) of a web service. However, users will not be able to benefitfrom these protection mechanisms unless they understand and are able to personalizepolicies applied in such contexts. For web services this includes policies for accesscontrol, privacy and business rules, among others.
This section summarizes research performed over the past years on semantic
policies and especially aim to analyse those aspects that did not receive so muchattention so far. We will focus our discussion on the following strategic goals andlines of research:
Rules-based policy representation: Rule-based languages are commonly regardedas the best approach to formalizing policies due to its flexibility, formal semanticsand closeness to the way people think.
Adoption of a broad notion of policy, encompassing not only access control poli-cies, but also privacy policies, business rules, quality of service, and others. Webelieve that all these different kinds of policies should eventually be integratedinto a single framework.
Strong and lightweight evidence: Policies make decisions based on properties ofthe peers interacting with the system. These properties may be strongly certifiedby cryptographic techniques, or may be reliable to some intermediate degreewith lightweight evidence gathering and validation. A flexible policy framework
Piero A. Bonatti and Daniel Olmedilla
should try to merge these two forms of evidence to meet the efficiency andusability requirements of web applications.
These desiderata imply that trust negotiation, reputation models, business rules,and action specification languages have to be integrated into a single frameworkat least to some extent. It is crucial to find the right tradeoff between generalityand efficiency. So far, no framework has tried to merge all aspects into a coherentsystem.
Automated trust negotiation is one of the main ingredients that can be used tomake heterogeneous peers effectively interoperate. This approach relies on andactively contributes to advances in the area of trust management.
Lightweight knowledge representation and reasoning does not only refer to com-putational complexity; it should also reduce the effort to specialize general frame-works to specific application domains; and the corresponding tools should be easyto learn and use for common users, with no particular training in computers orlogic. We regard these properties as crucial for the success of a semantic webframework.
The last issue cannot be tackled simply by adopting a rule language. Solutionslike controlled natural language syntax for policy rules, to be translated by aparser into the internal logical format, will definitively ease the adoption of anypolicy language.
Cooperative policy enforcement: A secure cooperative system should (almost)never say no. Web applications need to help new users in obtaining the servicesthat the application provides, so potential customers should not be discouraged.
Whenever prerequisites for accessing a service are not met, web applicationsshould explain what is missing and help the user in obtaining the required per-missions.
As part of cooperative enforcement, advanced explanation mechanisms are neces-sary to help users in understanding policy decisions and obtaining the permissionto access a desired service.
In the remainder of this section we describe the current state of the art on these
issues, expand on them and point out several interesting research directions relatedto them: the need for an flexible and easy policy representation, the different typesof policies which must be considered in order to address real world scenarios, theneed for strong and lightweight evidence on the information that policies require, theimportance of trust management as part of a policy framework, describing in detailnegotiations and provisional actions and how cooperative systems which explaintheir decisions to users as well as policy specification in natural language increaseuser awareness and understanding.
4.1 Rule-based policy representation
Rule-based languages are commonly regarded as the best approach to formalizingsecurity policies. In fact, most of the systems we use every day adopt policies for-mulated as rules. Roughly speaking, the access control lists applied by routers areactually rules of the form: "if a packet of protocol X goes from hosts Y to hosts Zthen [don't] let it pass". Some systems, like Java, adopt procedural approaches. Ac-cess control is enforced by pieces of code scattered around the virtual machine andthe application code; still, the designers of Java security felt the need for a method
Rule-Based Policy Representation and Reasoning for the Semantic Web
called implies, reminiscent of rules, that causes certain authorizations to entail otherauthorizations [32].
The main advantages of rule-based policy languages can be summarized as fol-
People (including users with no specific training in computers or logic) sponta-neously tend to formulate security policies as rules.
Rules have precise and relatively simple formal semantics, be it operational(rewrite semantics), denotational (fixpoint-based), or declarative (model the-oretic). Formal semantics is an excellent help in implementing and verifyingaccess control mechanisms, as well as validating policies.
Rule languages can be flexible enough to model in a unified framework the manydifferent policies introduced along the years as ad-hoc mechanisms. Differentpolicies can be harmonized and integrated into a single coherent specification.
In particular, logic programming languages are particularly attractive as policy spec-ification languages. They enjoy the above properties and have efficient inferencemechanisms (linear or quadratic time). This property is important as in most sys-tems policies have to manage a large number of users, files, and operations—hencea large number of possible authorizations. And for those applications where lineartime is too slow, there exist well-established compilation techniques (materialization,partial evaluation) that may reduce reasoning to pure retrieval at run time.
Another fundamental property of logic programs is that their inference is non-
monotonic, due to negation-as-failure. Logic programs can make default decisions inthe absence of complete specifications. Default decisions arise naturally in real-worldsecurity policies. For example, open policies prescribe that authorizations by defaultare granted, whereas closed policies prescribe that they should be denied unlessstated otherwise. Other nonmonotonic inferences, such as authorization inheritanceand overriding, are commonly supported by policy languages.
For all of these reasons, rule languages based on nonmonotonic logics eventually
became the most frequent choice in the literature. A popular choice consists ofnormal logic programs, i.e. sets of rules like
interpreted with the stable model semantics [33]. In general, each program may haveone stable model, many stable models, or none at all. There are opposite points ofview on this feature.
Some authors regard multiple models as an opportunity to write nondeterminis-
tic specifications where each model is an acceptable policy and the system makes anautomatic choice between the available alternatives [34]. For instance, the modelsof a policy may correspond to all possible ways of assigning permissions that pre-serve a Chinese Wall policy [35]. However, the set of alternative models may growexponentially, and the problem of finding one of them is NP-complete. There areexceptions with polynomial complexity [36, 37], though.
Some authors believe that security managers would not trust the system's auto-
matic choice and adopt restrictions such as stratifiability [38] to guarantee that thecanonical model be unique. The system rejects non-stratified specifications, high-lighting nonstratified rules to help the security administrator in reformulating thespecifications. As a further advantage, stratifiability-like restrictions yield PTIMEsemantics.
Piero A. Bonatti and Daniel Olmedilla
4.2 A broad notion of policy
Policies are pervasive in all web-related contexts. Access control policies are neededto protect any system open to the internet. Privacy policies are needed to assistusers while they are browsing the web and interacting with web services. Busi-ness rules specify which conditions apply to each customer of a web service. Otherpolicies specify constraints related to Quality of Service (QoS). In E-governmentapplications, visas and other documents are released according to specific eligibilitypolicies. This list is not exhaustive and is limited only by the class of applicationsthat can be deployed in the world wide web.
Most of these policies make their decisions based on similar pieces of informa-
tion [39] – essentially, properties of the peers involved in the transaction. For exam-ple, age, nationality, customer profile, identity, and reputation may all be consideredboth in access control decisions, and in determining which discounts are applicable(as well as other eligibility criteria). It is appealing to integrate these kinds of poli-cies into a coherent framework, so that (i) a common infrastructure can be used tosupport interoperability and decision making, and (ii) the policies themselves canbe harmonized and synchronized.
In the general view depicted above, policies may also establish that some events
must be logged (audit policies), that user profiles must be updated, and that when atransaction fails, the user should be told how to obtain missing permissions. In otherwords, policies may specify actions whose execution may be interleaved with thedecision process. Such policies are called provisional policies. In this context, policiesact both as decision support systems and as declarative behavior specifications. Aneffective user-friendly approach to policy specification could give common users (withno training in computer science or logic) better control on the behavior of their ownsystem (see the discussion in Section 4.5).
Of course, the extent to which this goal can be achieved depends on the policy's
ability to interoperate with legacy software and data – or more generally, with therest of the system. Then a policy specification language should support suitableprimitives for interacting with external packages and data in a flexible way.
The main challenges raised by these issues are then the following:
Harmonizing security and privacy policies with business rules, provisional poli-cies, and other kinds of policy is difficult because their standard formalizationsare based on different derivation strategies, and even different reasoning mech-anisms (cf. Section 4.4). Deduction, abduction, and event-condition-action rulesemantics need to be integrated into a coherent framework, trying to minimizesubtleties and technical intricacies (otherwise the framework would not be ac-cessible to common users).
Interactions between a rule-based theory and "external" software and data havebeen extensively investigated in the framework of logic-based mediation andlogic-based agent programming [40, 41]. However, there are novel issues relatedto implementing high-level policy rules with low-level mechanisms such as fire-walls, web server and DBMS security mechanisms, and operating system fea-tures, that are often faster and more difficult to bypass than rule interpreters[42]. A convincing realization of this approach might boost the application ofthe rich and flexible languages developed by the security community.
Rule-Based Policy Representation and Reasoning for the Semantic Web
4.3 Strong and lightweight evidence
Currently two major approaches for managing trust exist: policy-based and reputation-based trust management. The two approaches have been developed within the con-text of different environments and target different requirements. On the one hand,policy-based trust relies on "strong security" mechanisms such as signed certificatesand trusted certification authorities (CAs) in order to regulate access of users to ser-vices. Moreover, access decisions are usually based on mechanisms with well definedsemantics (e.g., logic programming) providing strong verification and analysis sup-port. The result of such a policy-based trust management approach usually consistsof a binary decision according to which the requester is trusted or not, and thusthe service (or resource) is allowed or denied. On the other hand, reputation-basedtrust relies on a "soft computational" approach to the problem of trust. In this case,trust is typically computed from local experiences together with the feedback givenby other entities in the network. For instance, eBay buyers and sellers rate eachother after each transaction. The ratings pertaining to a certain seller (or buyer) areaggregated by eBay's reputation system into a number reflecting seller (or buyer)trustworthiness as judged by the eBay community. The reputation-based approachhas been favored for environments such as Peer-to-Peer or Semantic Web, where theexistence of certifying authorities can not always be assumed but where a large poolof individual user ratings is often available.
Another approach – very common in today's applications – is based on forcing
users to commit to contracts or copyrights by having users click an "accept" buttonon a pop-up window. This is perhaps the lightest approach to trust, that can begeneralized by having users utter declarations (on their e-mail address, on theirpreferences, etc.) e.g. by filling an HTML form.
Real life scenarios often require to make decisions based on a combination of
these approaches. Transaction policies must handle expenses of all magnitudes, frommicropayments (e.g. a few cents for a song downloaded to your iPod) to credit cardpayments of a thousand euros (e.g. for a plane ticket) or even more. The cost ofthe traded goods or services contributes to determine the risk associated to thetransaction and hence the trust measure required.
Strong evidence is generally harder to gather and verify than lightweight evi-
dence. Sometimes, a "soft" reputation measure or a declaration in the sense outlinedabove is all one can obtain in a given scenario. We believe that the success of a trustmanagement framework will be determined by the ability of balancing trust levelsand risk levels for each particular task supported by the application, adding thefollowing to the list of interesting research directions:
How should different forms of trust be integrated? Some hints on modelling con-text aware trust, recommendation and risk with rules is given in [26] and a firstproposal for a full integration in a policy framework can be found in [43]. How-ever, new reputation models are being introduced, and there is a large numberof open research issues in the reputation area (e.g., vulnerability to coalitions).
Today, it is not clear which of the current approaches will be successful and howthe open problems will be solved. Any proposal should therefore aim at maximalmodularity in the integration of numerical and logical trust.
How many different forms of evidence can be conceived? In principle, propertiesof (and statements about) an individual can be extracted from any – possiblyunstructured – web resource. Supporting such a variety of information in policy
Piero A. Bonatti and Daniel Olmedilla
decisions is a typical semantic web issue – and an intriguing one. However, suchgeneral policies are not even vaguely as close to become real as the policies basedon more "traditional" forms of evidence (see the discussion in the next section).
4.4 Trust management
During the past few years, some of the most innovative ideas on security policiesarose in the area of automated trust negotiation [44, 8, 45, 7, 46, 47, 48, 49, 50].
That branch of research considers peers that are able to automatically negotiatecredentials according to their own declarative, rule-based policies. Rules specifyfor each resource or credential request which properties should be satisfied by thesubjects and objects involved. At each negotiation step, the next credential requestis formulated essentially by reasoning with the policy, e.g. by inferring implicationsor computing abductions.
Since about five years frameworks exist where credential requests are formulated
by exchanging sets of rules [8, 45]. Requests are formulated intensionally in order toexpress compactly and simultaneously all the possible ways in which a resource canbe accessed — shortening negotiations and improving privacy protection becausepeers can choose the best option from the point of view of sensitivity. It is notappealing to request "an ID and a credit card " by enumerating all possible pairsof ID credentials and credit card credentials; it is much better to define what IDsand credit cards are and send the definition itself. Another peer may use it to checkwhether some subset of its own credentials fulfills the request. This boils down togathering the relevant concept definitions in the policy (so-called abbreviation rules)and sending them to the other peer that reasons with those rules locally.
In [8, 45] peers communicate by sharing their ontologies. Interestingly, typical
policies require peers to have a common a priori understanding only of the predicaterepresenting credentials and arithmetic predicates, as any other predicate can beunderstood by sharing its definition. The only nontrivial knowledge to be shared isthe X.509 standard credential format. In this framework, interoperability based onontology sharing is already at reach! This is one of the aspects that make policies andautomated trust negotiation a most attractive application for semantic web ideas.
Another interesting proposal of [45] is the notion of declaration, that has already
been discussed in Section 4.3. This was the first step towards a more flexible andlightweight approach to policy enforcement, aiming at a better tradeoff betweenprotection efforts and risks. According to [51], this framework was one of the mostcomplete trust negotiation systems. The major limitation was the lack of distributednegotiations and credential discovery, which are now supported as specified in [8].
In response to a resource request, a web server may ask for credentials provingthat the client can access the resource. However, the credentials themselves can besensitive resources. So the two peers are in a completely symmetrical situation: theclient, in turn, asks the server for credentials (e.g. proving that it participates inthe Better Business Bureau program) before sending off the required credentials.
Each peer decides how to react to incoming requests according to a local policy,which is typically a set of rules written in some logic programming dialect. As we
Rule-Based Policy Representation and Reasoning for the Semantic Web
pointed out, requests are formulated by selecting some rules from the policies. Thisbasic schema has been refined along the years taking several factors into account[44, 8, 45, 7, 46, 47, 48, 49, 50].
First, policy rules may possibly inspect a local state (such as a legacy database)
that typically is not accessible by other peers. In that case, in order to make rulesintelligible to the recepient, they are partially evaluated with respect to the currentstate.
Second, policies themselves are sensitive resources, therefore not all relevant rules
are shown immediately to the peer. They are first filtered according to policy releaserules; the same schema may be applied to policy release rules themselves for anarbitrary but finite number of levels. As a consequence, some negotiations thatmight succeed, in fact fail just because the peers do not tell each other what theywant. The study of methodologies and properties that guarantee negotiation successis an interesting open research issue.
Moreover, credentials are not necessarily on the peer's host. It may be necessary
to locate them on the network [52]. As part of the automated support to cooperativeenforcement, peers may give each other hints on where a credential can be found[53].
There are further complications related to actions (cf. Section 4.4). In order
to tune the negotiation strategy to handle these aspects optimally, we can relyon a metapolicy language [8] that specifies which predicates are sensitive, which areassociated to actions, which peer is responsible for each action, and where credentialscan be searched for, guiding negotiation in a declarative fashion and making it morecooperative and interoperable. Moreover, the metapolicy language can be used toinstantiate the framework in different application domains and link predicates tothe ontologies where they are defined.
Provisional policies
Policies may state that certain requests or decisions have to be logged, or that thesystem itself should search for certain credentials. In other words, policy languagesshould be able to specify actions. Event-condition-action (ECA) rules constituteone possible approach. Another approach consists in labelling some predicates asprovisional, and associating them to actions that (if successful) make the predicatetrue [8]. We may also specify that an action should be executed by some other peer;this results in a request.
A cooperative peer tries to execute actions under its responsibility whenever
this helps in making negotiations succeed. For example, provisional predicates maybe used to encode business rules. The next rule5 enables discounts on low sellingarticles in a specific session:
allow(Srv ) ← . . , session(ID),
in(X , sql:query(′select ∗ from low selling′)),enabled(discount(X ), ID ) .
Intuitively, if enabled(discount(X ), ID) is not yet true but the other conditions
are verified, then the negotiator may execute the action associated to enabled and
5 formulated in Protune's language
Piero A. Bonatti and Daniel Olmedilla
the rule becomes applicable (if enabled(discount(X ), ID) is already true, no actionis executed). The (application dependent) action can be defined and associated toenabled through the metapolicy language. With the metalanguage one can alsospecify when an action is to be executed.
Some actions would be more naturally expressed as ECA rules. However, it is
not obvious how the natural bottom-up evaluation schema of ECA rules should beintegrated with the top-down evaluation adopted by the current core policy lan-guage. The latter fits more naturally the abductive nature of negotiation steps. Sointegration of ECA rules is still an interesting open research issue.
Stateful vs. stateless negotiations
Negotiations as described above are in general stateful, because (i) they may refer toa local state – including legacy software and data – and (ii) the sequence of requestsand counter requests may become more efficient if credentials and declarations arenot submitted again and again, but kept in a local negotiation state. However,negotiations are not necessarily stateful because
the server may refuse to answer counter-requests, or – alternatively – the cre-dentials and declarations disclosed during the transaction may be included inevery message and need not be cached locally;
the policy does not necessarily refer to external packages.
Stateless protocols are just special cases of the frameworks introduced so far.
Whether a stateless protocol is really more efficient depends on the application.
Moreover, efficiency at all costs might imply less cooperative systems.
Are stateful protocols related to scalability issues? We do not think so. The web
started as a stateless protocol, but soon a number of techniques were implemented tosimulate stateful protocols and transactions in quite a few real world applications andsystems, capable of answering a huge number of requests per time unit. We observethat if the support for stateful negotiations had been cast into http, probably manyof the intrinsic vulnerabilities of simulated solutions (like cookies) might have beenavoided.
Existing approaches to trust management and trust negotiation already tackle theneed for flexible, knowledge-based interoperability, and take into account the mainidiosyncrasies of the web – because automated trust negotiation frameworks havebeen designed with exactly that scenario in mind. Today, to make a real contribution(even in the context of a policy-aware web), we should further perform research onthe open issues of trust management, including at least the following topics:
Negotiation success: how can we guarantee that negotiations succeed despite allthe difficulties that may interfere: rules not disclosed because of lack of trust;credentials not found because their repository is unknown. What kind of prop-erties of the policy protection policy and of the hints (see Section 4.4) guaranteea successful termination when the policy "theoretically" permits access to aresource?
Rule-Based Policy Representation and Reasoning for the Semantic Web
Optimal negotiations: which strategies optimize information disclosure duringnegotiation? Can reasonable preconditions prevent unnecessary information dis-closure?
In the presence of multiple ways of fulfilling a request, how should the clientchoose a response? We need both a language for expressing preferences, andefficient algorithms for solving the corresponding optimization problem. Whilethis negotiation step is more or less explicitly assumed by most approaches ontrust negotiation, there is no concrete proposal so far.
Additionally, integration of abductive semantics and ECA semantics is an open
issue, as we have pointed out in a previous section.
4.5 Cooperative policy enforcement
Cooperative enforcement involves both machine-to-machine and human-machine as-pects. The former is handled by negotiation mechanisms: published policies, provi-sional actions, hints, and other metalevel information (see Section 4.4) can be in-terpreted by the client to identify what information is needed to access a resource,and how to obtain that information.
Let us discuss the human-machine interaction aspect in more detail: One of the
most important causes of the enormous number of computer security violations onthe Internet is the users' lack of technical expertise. Users are typically not awareof the security policies applied by their system, neither of course about how thosepolicies can be changed and how they might be improved by tailoring them tospecific needs. As a consequence, most users ignore their computer's vulnerabilitiesand the corresponding countermeasures, so the system's protection facilities cannotbe effectively exploited.
It is well known that the default, generic policies that come with system instal-
lations – often biased toward functionality rather than protection – are significantlyless secure than a policy specialized to a specific context, but very few users knowhow to tune or replace the default policy. Moreover, users frequently do not under-stand what the policy really checks, and hence are unaware of the risks involved inmany common operations.
Similar problems affect privacy protection. In trust negotiation, credential re-
lease policies are meant to achieve a satisfactory tradeoff between privacy and func-tionality – many interesting services cannot be obtained without releasing someinformation about the user. However, we cannot expect such techniques to be effec-tive unless users are able to understand and possibly personalize the privacy policyenforced by their system.
A better understanding of a web service's policy makes it also easier for a first-
time user to interact with the service. If denied access results simply in a "no"answer, the user has no clue on how he or she can possibly acquire the permissionto get the desired service (e.g., by completing a registration procedure, by supplyingmore credentials or by filling in some form). This is why we advocate cooperativepolicy enforcement, where negative responses are enriched with suggestions and otherexplanations whenever such information does not violate confidentiality (sometimes,part of the policy itself is sensitive).
For these reasons, greater user awareness and control on policies is one of our
main objectives, making policies easier to understand and formulate to the commonuser in the following ways:
Piero A. Bonatti and Daniel Olmedilla
Adopt a rule-based policy specification language, because these languages areflexible and at the same time structurally similar to the way in which policiesare expressed by nontechnical users.
Make the policy specification language more friendly by e.g. developing a con-trolled natural language front-end to translate natural language text into exe-cutable rules (see next section).
Develop advanced explanation mechanisms [24, 54, 55] to help the user under-stand what policies prescribe and control.
Inference Web (IW) [54, 55] is a toolkit that aims at providing useful explana-
tions for the behavior of (Semantic-) Web based systems. In particular, [54] proposesupport for knowledge provenance information using metadata (e.g., Dublin Coreinformation) about the distributed information systems involved in a particular rea-soning task. [54] also deals with the issue of representing heterogeneous reasoningapproaches, domain description languages and proof representations; the latter issueis addressed by using PML, the OWL-based Proof Markup Language [56].
Specifically applied to policies, [24] contains a requirements analysis for explana-
tions in the context of automated trust negotiation and defines explanation mech-anisms for why, why-not, how-to, and what-if queries. Several novel aspects aredescribed:
Adoption of a tabled explanation structure as opposed to more traditional ap-proaches based on single derivations or proof trees. The tabled approach makesit possible to describe infinite failures, which is essential for why not queries.
Explanations show simultaneously different possible proof attempts and allowusers to see both local and global proof details at the same time. This combi-nation of local and global (intra-proof and inter-proof) information facilitatesnavigation across the explanation structures.
Introduction of suitable heuristics for focussing explanations by removing irrel-evant parts of the proof attempts. A second level of explanations can recovermissing details, if desired.
Heuristics are generic, i.e. domain independent, they require no manual config-uration.
The combination of tabling techniques and heuristics yields a novel method forexplaining failure.
Explanation mechanisms should be lightweight and scalable in the sense that (i)
they do not require any major effort when the general framework is instantiatedin a specific application domain, and (ii) most of the computational effort can bedelegated to the clients. Queries are answered using the same policy specificationsused for negotiation. Query answering is conceived for the following categories ofusers:
Users who try to understand how to obtain access permissions;
Users who monitor and verify their own privacy policy;
Policy managers who verify and monitor their policies.
Currently, advanced queries comprise why/why not, how-to, and what-if queries.
Why/why not queries can be used by security managers to understand why somespecific request has been accepted or rejected, which may be useful for debuggingpurposes. Why-not queries may help a user to understand what needs to be done
Rule-Based Policy Representation and Reasoning for the Semantic Web
in order to obtain the required permissions, a process that in general may include acombination of automated and manual actions. Such features are absolutely essentialto enforce security requirements without discouraging users that try to connect toa web service for the first time. How-to queries have a similar role, and differ fromwhy-not queries mainly because the former do not assume a previous query as acontext, while the latter do.
What-if queries are hypothetical queries that allow to predict the behavior of a
policy before credentials are actually searched for and before a request is actuallysubmitted. What-if queries are good both for validation purposes and for helpingusers in obtaining permissions.
Among the technical challenges related to explanations, we mention:
Find the right tradeoff between explanation quality and the effort for instantiat-ing the framework in new application domains. Second generation explanationsystems [57, 58, 59] prescribe a sequence of expensive steps, including the cre-ation of an independent domain knowledge base expressly for communicatingwith the user. This would be a serious obstacle to the applicability of the frame-work.
Natural language policies
Policies should be written by and understandable to users, to let them control be-havior of their system. Otherwise the risk that users keep on adopting generic henceineffective built-in policies, and remain unaware of which controls are actually madeby the system is extremely high – and this significantly reduces the benefits of aflexible policy framework.
Most users have no specific training in programming nor in formal logics. Fortu-
nately, they spontaneously tend to formulate policies as rules; still, logical languagesmay be intimidating. For this reason, the design of front ends based on graphicalformalisms as well as natural language interfaces are crucial to the adoption of for-mal policy languages. We want policy rules to be formulated like: "Academic userscan download the files in folder historical data whenever their creation date precedes1942 ".
Clearly, the inherent ambiguity of natural language is incompatible with the
precision needed by security and privacy specifications. Solutions to that can be theadoption of a controlled fragment of English (e.g., the Attempto system6) where afew simple rules determine a unique meaning for each sentence. This approach can becomplemented with a suitable interface that clarifies what the machine understands.
Policies are really knowledge bases: a single body of declarative rules used in manypossible ways, for negotiations, query answering, and other forms of system behaviorcontrol. As far as trust negotiation is concerned, we further argue that transparentinteroperation based on ontology sharing can become "everyday technology" in a
Piero A. Bonatti and Daniel Olmedilla
short time, and trust negotiation especially will become a success story for semanticweb ideas and techniques.
In addition to stateless negotiation [60], we need stateful negotiation as well [45].
Even the Web, which started as a stateless protocol, now implements a number oftechniques to simulate stateful protocols and transactions, especially in applicationsfor accessing data other than web pages.
Cooperative policy enforcement and trust management gives common users bet-
ter understanding and control on the policies that govern their systems and theservices they interact with. The closer we get to this objective, the higher the im-pact of our techniques and ideas will be.
Policies will have to handle decisions under a wide range of risk levels, perfor-
mance requirements, and traffic patterns. It is good to know that the rule-basedtechniques that different research communities are currently converging to are pow-erful enough to effectively address such a wide spectrum of scenarios. This is thelevel of flexibility needed by the Semantic Web.
About This Manuscript
This manuscript provides an introduction to policy representation and reasoningfor the Semantic Web. It describes the benefits of using policies and presents fourof the most relevant policy languages. These four languages are classified accordingto whether policies are assumed to be public or else may be protected. The formerconsists of a single evaluation step where a policy engine or a matchmaker decideswhether two policies are compatible or not. Examples of this kind of evaluation arethe KAOS and REI frameworks. If policies may be protected (by e.g. other policies),the process is not anymore a one-step evaluation. In this case, policies guide anegotiation in which policies are disclosed iteratively increasing the level of securityat each step towards a final agreement. Examples of these kind of frameworks arePeerTrust and Protune. Furthermore, Semantic Web techniques can be used to easeand enhance the process of policy specification and validation. Conflicts betweenpolicies can be found and even resolved automatically (either by meta-policies or byharmonisation algorithms).
In order to demonstrate the benefits and feasibility of Semantic Web policies,
several application scenarios are briefly described, namely the (Semantic) Web, (Se-mantic) Web Services and the (Semantic) Grid. Finally a list of open research issuesthat prevent existing policy languages from being widely adopted are introduced.
This list is intended to help new researchers in the area to focus on those crucialproblems which are still unsolved.
1. Tim Berners-Lee, James Hendler, and Ora Lassila. The Semantic Web. Scien-
tific American, may 2001.
2. Grigoris Antoniou, Matteo Baldoni, Piero A. Bonatti, Wolfgang Nejdl, and
Daniel Olmedilla. Rule-based policy specification. In Ting Yu and Sushil Jajo-dia, editors, Secure Data Management in Decentralized Systems, volume 33 ofAdvances in Information Security. Springer, 2007.
Rule-Based Policy Representation and Reasoning for the Semantic Web
3. Matt Blaze, Joan Feigenbaum, and Angelos D. Keromytis. Keynote: Trust man-
agement for public-key infrastructures (position paper). In Security Protocols,6th International Workshop, volume 1550 of Lecture Notes in Computer Science,pages 59–63, Cambridge, April, 1998. Springer.
4. Matt Blaze, Joan Feigenbaum, and Martin Strauss. Compliance checking in
the policymaker trust management system. In Financial Cryptography, SecondInternational Conference, volume 1465 of Lecture Notes in Computer Science,pages 254–274, Anguilla, British West Indies, February 1998. Springer.
5. Andrzej Uszok, Jeffrey M. Bradshaw, Renia Jeffers, Niranjan Suri, Patrick J.
Hayes, Maggie R. Breedy, Larry Bunch, Matt Johnson, Shriniwas Kulkarni,and James Lott. KAoS policy and domain services: Toward a description-logicapproach to policy representation, deconfliction, and enforcement. In POLICY,page 93, 2003.
6. Lalana Kagal, Timothy W. Finin, and Anupam Joshi. A policy based approach
to security for the semantic web. In The Semantic Web - ISWC 2003, Sec-ond International Semantic Web Conference, Sanibel Island, FL, USA, October20-23, 2003, Proceedings, Lecture Notes in Computer Science, pages 402–418.
Springer, 2003.
7. Rita Gavriloaie, Wolfgang Nejdl, Daniel Olmedilla, Kent E. Seamons, and Mar-
ianne Winslett. No registration needed: How to use declarative policies andnegotiation to access sensitive resources on the semantic web. In 1st EuropeanSemantic Web Symposium (ESWS 2004), volume 3053 of Lecture Notes in Com-puter Science, pages 342–356, Heraklion, Crete, Greece, May 2004. Springer.
8. Piero A. Bonatti and Daniel Olmedilla. Driving and monitoring provisional
trust negotiation with metapolicies. In 6th IEEE International Workshop onPolicies for Distributed Systems and Networks (POLICY 2005), pages 14–23,Stockholm, Sweden, June 2005. IEEE Computer Society.
9. Gianluca Tonti, Jeffrey M. Bradshaw, Renia Jeffers, Rebecca Montanari, Niran-
jan Suri, and Andrzej Uszok. Semantic web languages for policy representationand reasoning: A comparison of KAoS, Rei, and Ponder. In International Se-mantic Web Conference, pages 419–437, 2003.
10. Lalana Kagal, Massimo Paolucci, Naveen Srinivasan, Grit Denker, Timothy W.
Finin, and Katia P. Sycara. Authorization and privacy for semantic web services.
IEEE Intelligent Systems, 19(4):50–56, 2004.
11. K. Taveter and G. Wagner. Agent-oriented enterprise modeling based on busi-
ness rules. In ER '01: Proceedings of the 20th International Conference onConceptual Modeling, pages 527–540. Springer-Verlag, 2001.
12. William H. Winsborough, Kent E. Seamons, and Vicki E. Jones. Automated
trust negotiation. DARPA Information Survivability Conference and Exposi-tion, IEEE Press, Jan 2000.
13. Wolfgang Nejdl, Daniel Olmedilla, Marianne Winslett, and Charles C. Zhang.
Ontology-based policy specification and management. In 2nd European Se-mantic Web Conference (ESWC), volume 3532 of Lecture Notes in ComputerScience, pages 290–302, Heraklion, Crete, Greece, May 2005. Springer.
14. Piero A. Bonatti, Claudiu Duma, Norbert Fuchs, Wolfgang Nejdl, Daniel
Olmedilla, Joachim Peer, and Nahid Shahmehri. Semantic web policies - adiscussion of requirements and research issues. In 3rd European Semantic WebConference (ESWC), volume 4011 of Lecture Notes in Computer Science, Budva,Montenegro, June 2006. Springer.
Piero A. Bonatti and Daniel Olmedilla
15. Daniel Olmedilla. Security and privacy on the semantic web. In Milan Petkovic
and Willem Jonker, editors, Security, Privacy and Trust in Modern Data Man-agement. Springer, 2007 (to appear).
16. Jeffrey M. Bradshaw, Andrzej Uszok, Renia Jeffers, Niranjan Suri, Patrick J.
Hayes, Mark H. Burstein, Alessandro Acquisti, Brett Benyo, Maggie R. Breedy,Marco M. Carvalho, David J. Diller, Matt Johnson, Shriniwas Kulkarni, JamesLott, Maarten Sierhuis, and Ron van Hoof. Representation and reasoning forDAML-based policy and domain services in KAoS and nomads. In The SecondInternational Joint Conference on Autonomous Agents & Multiagent Systems(AAMAS), pages 835–842, Melbourne, Victoria, Australia, jul 2003. ACM.
17. Mike Dean and Guus Schreiber. OWL web ontology language reference, 2004.
18. Franz Baader, Diego Calvanese, Deborah L. McGuinness, Daniele Nardi, and
Peter F. Patel-Schneider, editors. The Description Logic Handbook: Theory,Implementation, and Applications. Cambridge University Press, 2003.
19. Lalana Kagal. A Policy-Based Approach to Governing Autonomous Behaviour
in Distributed Environments. PhD thesis, University of Maryland BaltimoreCounty, 2004.
20. P. Bonatti and P. Samarati. Regulating Service Access and Information Re-
lease on the Web. In Conference on Computer and Communications Security(CCS'00), Athens, November 2000.
21. N. Li and J.C. Mitchell. RT: A Role-based Trust-management Framework. In
DARPA Information Survivability Conference and Exposition (DISCEX), Wash-ington, D.C., April 2003.
22. Jim Trevor and Dan Suciu. Dynamically distributed query evaluation. In
Proceedings of the twentieth ACM SIGMOD-SIGACT-SIGART Symposium onPrinciples of Database Systems, Santa Barbara, CA, USA, May 2001.
23. Miguel Alves, Carlos Viegas Dam´
asio, Wolfgang Nejdl, and Daniel Olmedilla. A
distributed tabling algorithm for rule based policy systems. In 7th IEEE Inter-national Workshop on Policies for Distributed Systems and Networks (POLICY2006), pages 123–132, London, Ontario, Canada, June 2006. IEEE ComputerSociety.
24. Piero A. Bonatti, Daniel Olmedilla, and Joachim Peer. Advanced policy ex-
planations on the web. In 17th European Conference on Artificial Intelligence(ECAI 2006), pages 200–204, Riva del Garda, Italy, Aug-Sep 2006. IOS Press.
25. Pranam Kolari, Li Ding, Shashidhara Ganjugunte, Anupam Joshi, Timothy W.
Finin, and Lalana Kagal. Enhancing web privacy protection through declara-tive policies. In 6th IEEE International Workshop on Policies for DistributedSystems and Networks (POLICY 2005), pages 57–66, Stockholm, Sweden, jun2005. IEEE Computer Society.
26. Steffen Staab, Bharat K. Bhargava, Leszek Lilien, Arnon Rosenthal, Marianne
Winslett, Morris Sloman, Tharam S. Dillon, Elizabeth Chang, Farookh KhadeerHussain, Wolfgang Nejdl, Daniel Olmedilla, and Vipul Kashyap. The puddingof trust. IEEE Intelligent Systems, 19(5):74–88, 2004.
27. Grit Denker, Lalana Kagal, Timothy W. Finin, Massimo Paolucci, and Katia P.
Sycara. Security for daml web services: Annotation and matchmaking. In TheSemantic Web - ISWC 2003, Second International Semantic Web Conference,Sanibel Island, FL, USA, October 20-23, 2003, Proceedings, Lecture Notes inComputer Science, pages 335–350. Springer, 2003.
28. Daniel Olmedilla, Rub´en Lara, Axel Polleres, and Holger Lausen. Trust nego-
tiation for semantic web services. In 1st International Workshop on Semantic
Rule-Based Policy Representation and Reasoning for the Semantic Web
Web Services and Web Process Composition (SWSWPC), volume 3387 of Lec-ture Notes in Computer Science, pages 81–95, San Diego, CA, USA, July 2004.
Springer.
29. Grid Security Infrastructure. http://www.globus.org/security/overview.html.
30. Andrzej Uszok, Jeffrey M. Bradshaw, and Renia Jeffers. Kaos: A policy and
domain services framework for grid computing and semantic web services. InTrust Management, Second International Conference, iTrust 2004, Oxford, UK,March 29 - April 1, 2004, Proceedings, Lecture Notes in Computer Science,pages 16–26. Springer, 2004.
31. Ionut Constandache, Daniel Olmedilla, and Wolfgang Nejdl. Policy based dy-
namic negotiation for grid services authorization. In Semantic Web Policy Work-shop in conjunction with 4th International Semantic Web Conference, Galway,Ireland, November 2005.
32. Li Gong. Inside Java 2 Platform Security: Architecture, API Design, and Im-
plementation. Addison-Wesley, 1999.
33. M. Gelfond and V. Lifschitz. The stable model semantics for logic programming.
In Proc. of the 5th ICLP, pages 1070–1080. MIT Press, 1988.
34. Elisa Bertino, Elena Ferrari, Francesco Buccafurri, and Pasquale Rullo. A logical
framework for reasoning on data access control policies. In Proc. of the 12thIEEE Computer Security Foundations Workshop (CSFW'99), pages 175–189.
IEEE Computer Society, 1999.
35. D. F. C. Brewer and M. J. Nash. The chinese wall security policy. In IEEE
Symposium on Security and Privacy, pages 206–214, 1989.
36. Luigi Palopoli and Carlo Zaniolo. Polynomial-time computable stable models.
Ann. Math. Artif. Intell., 17(3-4):261–290, 1996.
37. Domenico Sacc
a and Carlo Zaniolo. Stable models and non-determinism in
logic programs with negation. In Proc. of the Ninth ACM SIGACT-SIGMOD-SIGART Symposium on Principles of Database Systems (PODS'90), pages 205–217, 1990.
38. Krzysztof R. Apt, Howard A. Blair, and Adrian Walker. Towards a theory
of declarative knowledge. In Foundations of Deductive Databases and LogicProgramming., pages 89–148. Morgan Kaufmann, 1988.
39. P. A. Bonatti, N. Shahmehri, C. Duma, D. Olmedilla, W. Nejdl, M. Bal-
doni, C. Baroglio, A. Martelli, V. Patti, P. Coraggio, G. Antoniou, J. Peer,and N. E. Fuchs. Rule-based policy specification: State of the art and futurework. Technical report, Working Group I2, EU NoE REWERSE, August 2004.
http://rewerse.net/deliverables/i2-d1.pdf.
40. V.S. Subrahmanian, S. Adali, A. Brink, R. Emery, J.J. Lu, A. Rajput, T.J.
Rogers, R. Ross, and C. Ward. Hermes: Heterogeneous reasoning and media-tor system. http://www.cs.umd.edu/projects/publications/ abstracts/hermes.
html.
41. V. S. Subrahmanian, Piero A. Bonatti, J¨
urgen Dix, Thomas Eiter, Sarit Kraus,
Fatma Ozcan, and Robert Ross. Heterogenous Active Agents. MIT Press, 2000.
42. Arnon Rosenthal and Marianne Winslett. Security of shared data in large sys-
tems: State of the art and research directions. In Proceedings of the ACM SIG-MOD International Conference on Management of Data, Paris, France, June13-18, 2004, pages 962–964. ACM, 2004.
43. Piero A. Bonatti, Claudiu Duma, Daniel Olmedilla, and Nahid Shahmehri. An
integration of reputation-based and policy-based trust management. In Seman-
Piero A. Bonatti and Daniel Olmedilla
tic Web Policy Workshop in conjunction with 4th International Semantic WebConference, Galway, Ireland, November 2005.
44. M. Blaze, J. Feigenbaum, and M. Strauss. Compliance Checking in the Poli-
cyMaker Trust Management System. In Financial Cryptography, British WestIndies, February 1998.
45. P.A. Bonatti and P. Samarati. A uniform framework for regulating service access
and information release on the web. Journal of Computer Security, 10(3):241–272, 2002. Short version in the Proc. of the Conference on Computer andCommunications Security (CCS'00), Athens, 2000.
46. W. Winsborough, K. Seamons, and V. Jones. Negotiating Disclosure of Sensitive
Credentials. In Second Conference on Security in Communication Networks,Amalfi, Italy, September 1999.
47. W. Winsborough, K. Seamons, and V. Jones. Automated Trust Negotiation.
In DARPA Information Survivability Conference and Exposition, Hilton HeadIsland, SC, January 2000.
48. Marianne Winslett, Ting Yu, Kent E. Seamons, Adam Hess, Jared Jacobson,
Ryan Jarvis, Bryan Smith, and Lina Yu. Negotiating trust on the web. IEEEInternet Computing, 6(6):30–37, 2002.
49. Ting Yu, Marianne Winslett, and Kent E. Seamons. Supporting structured
credentials and sensitive policies through interoperable strategies for automatedtrust negotiation. ACM Trans. Inf. Syst. Secur., 6(1):1–42, 2003.
50. M. Y. Becker and P. Sewell. Cassandra: distributed access control policies with
tunable expressiveness. In 5th IEEE International Workshop on Policies forDistributed Systems and Networks, Yorktown Heights, June 2004.
51. K. Seamons, M. Winslett, T. Yu, B. Smith, E. Child, J. Jacobsen, H. Mills, and
L. Yu. Requirements for Policy Languages for Trust Negotiation. In 3rd Inter-national Workshop on Policies for Distributed Systems and Networks, Monterey,CA, June 2002.
52. N. Li, W. Winsborough, and J.C. Mitchell. Distributed Credential Chain Dis-
covery in Trust Management (Extended Abstract). In ACM Conference onComputer and Communications Security, Philadelphia, Pennsylvania, Novem-ber 2001.
53. C. Zhang, P.A. Bonatti, and M. Winslett. Peeraccess: A logic for distributed
authorization. In 12th ACM Conference on Computer and Communication Se-curity (CCS 2005), Alexandria, VA, USA, 2005. ACM.
54. Deborah L. McGuinness and Paulo Pinheiro da Silva. Explaining answers from
the semantic web: The inference web approach. Journal of Web Semantics,1(4):397–413, 2004.
55. Deborah L. McGuinness and Paulo Pinheiro da Silva. Trusting answers from
web applications. In New Directions in Question Answering, pages 275–286,2004.
56. Paulo P. da Silva, Deborah L. McGuinness, and Richard Fikes. A proof markup
language for semantic web services. Technical Report KSL Tech Report KSL-04-01, January, 2004.
57. William Swartout, Cecile Paris, and Johanna Moore. Explanations in knowl-
edge systems: Design for explainable expert systems. IEEE Expert: IntelligentSystems and Their Applications, 6(3):58–64, 1991.
58. Michael C. Tanner and Anne M. Keuneke. Explanations in knowledge systems:
The roles of the task structure and domain functional models. IEEE Expert:Intelligent Systems and Their Applications, 6(3):50–57, 1991.
Rule-Based Policy Representation and Reasoning for the Semantic Web
59. M. R. Wick. Second generation expert system explanation. In J.-M. David, J.-
P. Krivine, and R. Simmons, editors, Second Generation Expert Systems, pages614–640. Springer Verlag, 1993.
60. Vladimir Kolovski, Yarden Katz, James Hendler, Daniel Weitzner, and Tim
Berners-Lee. Towards a policy-aware web. In Semantic Web Policy Workshop inconjunction with 4th International Semantic Web Conference, Galway, Ireland,nov 2005.
Source: http://www.l3s.de/~olmedilla/pub/2007/2007_ReasoningWeb-policies.pdf
cacy and safety of balloon kyphoplasty compared with non-surgical care for vertebral compression fracture (FREE): a randomised controlled trial Douglas Wardlaw, Steven R Cummings, Jan Van Meirhaeghe, Leonard Bastian, John B Tillman, Jonas Ranstam, Richard Eastell, Peter Shabe, Karen Talmadge, Steven Boonen Lancet 2009; 373: 1016–24
VOLUME 4 • NUMBER 1 • JANUARY 2005 Cosmetic Dermatology Edited by Zoe Diana Draelos Reprinted Article: Idebenone: a new antioxidant – Part I. Relative assessment of oxidativestress protection capacity compared to commonly known antioxidants D H McDaniel, B A Neudecker, J C DiNardo, J A Lewis, II & H I Maibach

